(CCNA Study Review #2)
Just a reminder to those following along these posts are a lot like my notebook. I might edit and change how the content is displayed based on what seems best.
Things Covered in this Article
- Recap of OSI and TCP
- Bits and Bytes
- Protocol Data Unit
- Segments
- Packets
- Frames
- Example of how it works
Recap
I covered this in my last post in much greater detail, so I highly suggest that you check it out there if you want.
Essentially the low-down is that OSI Model has 7 Layers to it and is the model that IT professionals use to better identify issues. TCP/IP model is the one that is actually used on the internet and has 4 Layers to it, but those 4 Layers just comprise the 7 Layers. (see below)
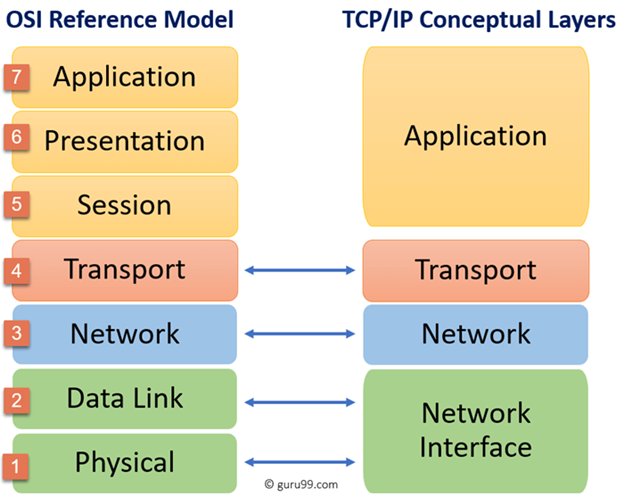
(Photo by Guru99 via https://www.guru99.com/)
Data when it is going from one network device to another (networked computers, switches, routers, etc.) uses this model to understand what you are looking for and who to get it from. So, when you google search “Why Isn’t 11 pronounced onety one”, your switch will look at the data and know to push it to your router to have your router look at it and push it out to the internet to get your answer.
Now I have been somewhat vague in how it looks at the data and knows, well that is where today’s topic comes in.
Bits and Bytes are what?
So, before we dig into the thick of how packets and all that work, we need to make sure we have a foundation of what data even is.
So, what is a Bit? Well, a Bit is the smallest unit of storage we have currently (Quantum Computing might shake this up in the future). In technology a Bit is simply a 0 or a 1, that can be represented in a couple different ways depending on the medium that is transferring the data.
An ethernet cable with coper wire in it, transfers the 0 and 1’s by simply being on or off. Somewhat like morse code but instead of dots and dashes it is simply dot or no dot. Fiber does the same just with light instead of electricity. In a hard drive it does it with magnetism using tiny spots of north or south.
So, a single Bit is either a 0 or a 1. Pretty useless on its own but put them into a chain and you can start having them represent something more. That is where Bytes (pronounced “bites”) come in.
A Byte is a group of eight Bits and with this grouping you get a lot more usability. When you have eight Bits that can be arranged in any way, you end up with a potential of 256 potential different patterns.
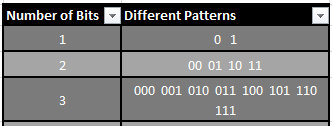
You can see how we easily get to 256 different combos quickly with eight Bits. But there are way more then 256 different things to represent in our world. Say we wanted to count to the number 3,156 then we would not be able to because we only have 256 options for representation. Therefore, a single Byte is useful for storing one typed character like a letter, but not something like a movie.
To store something like an image or movie we need more available options. We could go one of two different ways with this.
- Increase our Byte size to have more bits in it, say 16 Bits, giving us 65,536 potential options. But then say I only want to have the letter “A” represented. Using 16 Bits would mean that there would be a lot of wasted energy and efficiency because my “A” would have been transfer quickly at the beginning, but the rest of this theoretical “Byte” would have to finish before starting the next bit of data.
- Or we can leverage the same logic that we used to combine Bits into groups to create Bytes. We can group Bytes together to give us more options and flexibility. This is the option that was decided on because it gives more flexibility no matter the amount of data. However, in the end everything is calculated in the number of Bytes.
With that knowledge, the information below will make some more sense hopefully.
- Kilobyte (KB) = 1 thousand bytes (8 thousand bits)
- Megabyte (MB) = 1 million bytes (8 million bits)
- Gigabyte (GB) = 1 billion bytes (8 billion bits)
- Terabyte (TB) = 1 trillion bytes (8 trillion bits)
Take that in for a moment, when you download safe a 5 MB picture of a cat, there are millions of little bits of electricity going out the cable (or radio waves through the air if you are on Wi-Fi) all to get you that little cute picture.
There is a lot more to how bytes are used, like ASCII and UTF-8. However, for the purpose of this article this is what you need to know. Although at the end of this article I will link a cool resource as well.
Protocol Data Unit (PDU)
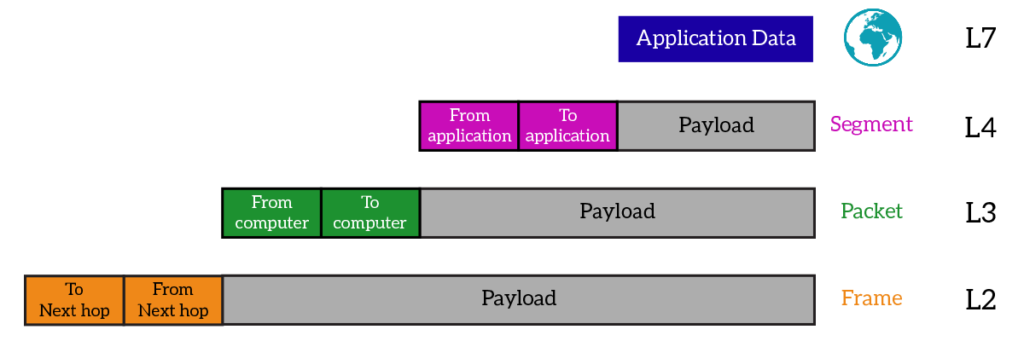
A Protocol Data Unit or PDU is a term that is used to refer to the data (composed of bytes) when iis at various layers of the OSI model. It is a common term for the terms packet, frame, and segment but you would call it a Transport Layer PDU, or a Network Layer PDU.
Segments
In the TCP model, the Application Layer is composed of the top 3 layers of the OSI model. This Application Layer will push data down to the Transport Layer, but the Transport Layer needs it broken up into a format that it can use. So, the TCP protocol (namesake of the model), comes in and breaks the data down into something called the Maximum Segment Size (MSS) that the network can handle. Thus, when data is at the Transport Layer it is called a Segment.

When the data is turned into a Segment, a “header” is attached onto the data. This header is what assists in helping the data get to whenever it is supposed to go. The normal size of a header can be anywhere from 20 bytes to 60 bytes.
Things in the header are:
- Source Port (Basically the address of the application on you computer that created the data)
- Destination Port (Address of the application the data is meant for)
- Flag bits (tells network devices if you can break the data up or not)
- Sequence Number of the Segments (Order the data should come in)
- Checksum (makes sure the correct data is sent and received)
- Options
Packets
After the Segment is formed it is then handed down to Network Layer. This layer is all about IP addresses and which computer is the data meant for. So the Network Layer adds on its own “header” that is usually about the same 20 Bytes to 60 Bytes in size.
Things in the header are:
- Source IP Address (Address of the computer the data is from)
- Destination IP Address (Address of the computer the data is supposed to go)
- Time to Leave “TTL” (Time the Data must go to the next network device or it will be eliminated to conserve network resources)
- Identification (A unique ID for each packet)
- Protocol Type (A TCP Packet or UDP packet)
- Version of the Protocol
- Options
Frames
Now that the data has what application and what computer it is from and it is supposed to go to, the only thing left is how to get it there. Devices on the network/internet are not able to keep huge lists of IP addresses for every device in the world, instead they keep their “Next Door Neighbors” addresses in a list and know who to pass the data to depending on the IP address. Media Access Control (MAC) addresses are unique identifiers that are different for every single networked device. No two are the same.

Things in the header are:
- Source MAC Address (Address of the device who had the data last)
- Destination MAC Address (Address of device the data is going to next)
- Length (the maximum transferable unit of the network)
- Checksum (error checking)
Example
Let us say that you live in Tampa Bay, Florida and you friend Sally lives in Columbus, Ohio. Both of you have the same coloring book, but your coloring book has one extra page in it. Your friend Sally wants you to send a copy of the page to her. So, you copy it and put it in an envelope on the back of which you write the name of the coloring book that the page goes into (because Sally is very forgetful).
Now with that settled you take that envelope and put it into another envelope and write Columbus, Ohio and Sally’s home address on it, (so everyone knows where it is supposed to go) and Tampa Bay, Florida with your home address (So everyone knows who it is from). Now there is no postal service so how are you going to get it there?
That is when you have a great idea, your friend Rob knows how to get things to Atlanta Georgia. So, you decide to take that envelope, put it in another envelope and you write Rob’s name on it and deliver it to his house.
Rob now has this envelope with his name on it, but he needs to know what to do with it. So, he takes that envelope off and sees that it is supposed to go to Ohio. Well, his friend Brian in Atlanta knows how to get things to places close to there. Therefore, he puts it in another envelope, writes Brian’s name on it and delivers it to Brian. Brian receives it and takes off the envelope and looks at the address, now he knows how to get to Sally, because he has delivered stuff there before, so he puts it in an envelope writes Sally’s name on it and delivers it to her.
Now Sally gets that envelope, sees her name on it so she takes the envelope off. On the next envelope she is like “Hey that is my address” so she takes that envelope off. Now she has the envelope calling out what coloring book and she is like “I have that coloring book!” so she takes that envelope off and has the coloring page she wanted, and she puts it into her coloring book.
(Photo via https://www.ictshore.com )
Closing Statment
For those of you that want to experience bytes and what maybe changing sentences into binary here is a website you can do that at…
https://www.rapidtables.com/convert/number/ascii-to-binary.html
Thank you for reading!
